The Greatest Guide To Aws Backup
Wiki Article
How Aws Backup can Save You Time, Stress, and Money.
Table of Contents10 Simple Techniques For Ec2 BackupThe Of Ransomware ProtectionThe 45-Second Trick For S3 Cloud BackupIndicators on Aws S3 Backup You Need To Know
Information defense is the process of protecting vital data from corruption, concession or loss and also giving the ability to restore the data to an useful state must something happen to provide the data hard to reach or pointless. Information protection ensures that data is not corrupted, comes for authorized objectives just, and remains in compliance with suitable legal or regulative needs (RTO).The scope of information protection, however, exceeds the notion of data schedule and also usability to cover areas such as information immutability, preservation, as well as deletion/destruction. About talking, data security extends three wide groups, namely, conventional information defense (such as backup and restore duplicates), data protection, and also data privacy as displayed in the Figure below. Number: The 3 Groups of Information Protection The principle of data security is to deploy methodologies as well as modern technologies to protect and make data offered under all scenarios. Storage space modern technologies can be made use of to safeguard information by using disk, tape or cloud backup to safely save copies of the information that can be used in case of data loss or disturbance.
, altered block tracking, and so on,) are supplying one more layer of information security in addition to typical backup.
The information storage market looks at information protection primarily from a technology perspective in what is required to maintain information secure and also available. Data security is specified by the European Union (EU) in an extremely different method and also is commonly used where other regions might use the term information privacy.
S3 Cloud Backup - Truths
Data goes to the facility of service. https://www.bookmarkinbox.info/author/clumi0/. For many organizations, digital fostering drives method. Data is vital to satisfying consumer requirements, responding to abrupt market shifts and also unanticipated occasions. That's why information defense must be on your mind. Enterprises produce large quantities of information from numerous sources. The large quantity as well as detail of venture information created throughout working needs recurring interest to exactly how you safeguard and keep it.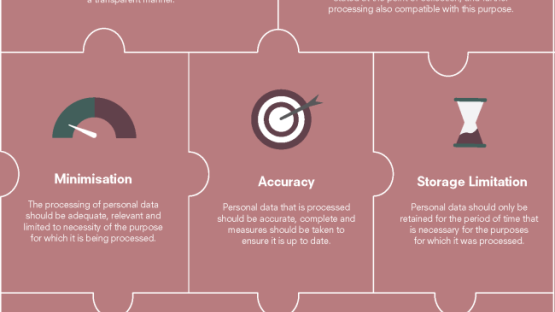
Today, it consists of Io, T devices and sensors, industrial machines, robotics, wearables as well as even more. Data security helps in reducing risk and also allows a business or company to react rapidly to hazards. Information defense is very important due to the fact that the overall variety of computer devices enhances yearly, and also computing is currently more complicated.
2 ZB of information was produced or replicated. Not all information developed in 2020 was kept, however IDC recommends there is enough proof keeping more information might profit ventures.
Indicators on Ec2 Backup You Need To Know
The manufacturing field has a tendency to invest less resources in safeguarding commercial procedures technology (OT) than in their venture networks. That leaves OT systems available to endanger. These OT systems include self-driving lorries, robotics, Industrial Io, T tools and sensing units. Important infrastructure counts on industrial control systems along with a great deal of different OT systems to operate.The production industry is a prominent strike target, too. In 2020, manufacturing, energy and also wellness treatment sectors dealt with the highest possible price of attack according to IBMs Annual X-Force Danger Index. Protecting company networks without offering the same attention to OT and tools opens them for a strike. Digital assets are rewarding targets, a lot more so as even more businesses work with digital growth initiatives attaching much more services.
Data safety and security for supply chains and third-party accessibility to systems is important to secure them from cyberattacks. Balancing compliance with meeting company purposes can be an obstacle if you do not have a data defense method in area.
The order concentrates on activities to strengthen cybersecurity with bringing important framework and also federal government networks up to modern-day criteria. This will just obtain more complicated as the federal government enacts new laws and more closely enforces older guidelines - https://www.artstation.com/matthewbrennan7/profile.
How Data Protection can Save You Time, Stress, and Money.
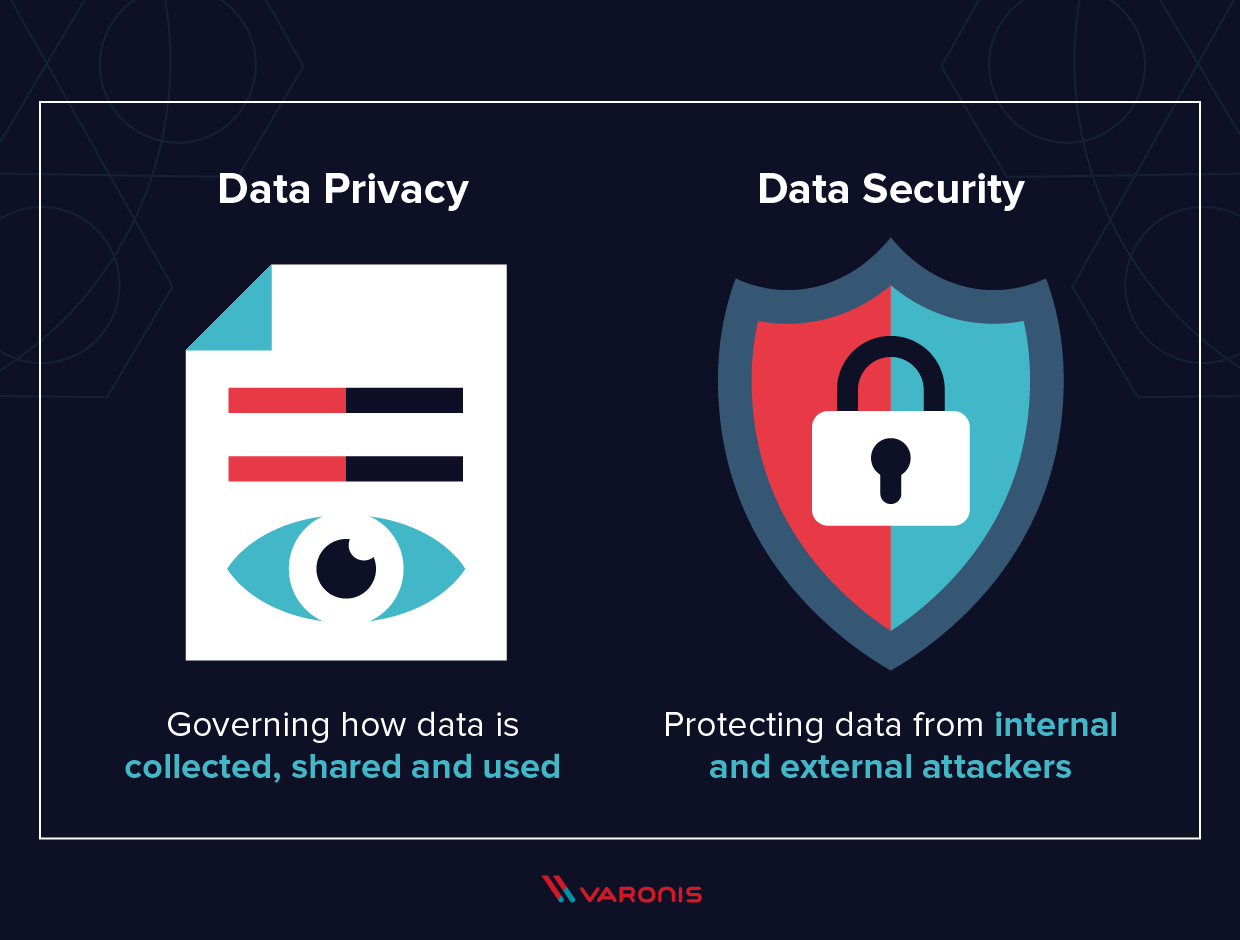
There stay no sweeping government regulations on customer information privacy securities (https://href.li/?https://clumio.com/). Information protection and data safety and security are comparable however unique. The previous is an approach of protecting information from undesirable gain access to, burglary as well as corruption from the minute a tool creates it until the moment of removal. Data safety exists in every element of info protection.A thorough data security approach shields electronic properties against strike while accounting for as well as protecting against insider dangers. (These remain to be a leading source of information violations each year.) Releasing data safety and security devices and also technologies provide services a means to evaluate essential information at its storage space places. They additionally aid gain insight into how people as well as tools are utilizing it.
Report this wiki page